Deprecate SMS OTP
Overview
Topics: consumer, passkey, WebAuthn, cost reduction
Customer journey: Awareness > Consideration > Enrollment > Management > Authentication
Created: 24 May 2024
Allow people to create a passkey to replace passwords plus SMS OTP authentication.
Add deprecate SMS OTP
- Replace the poor user experience, phishing-prone security, and high costs of SMS OTP authentication.
- Introduce passkeys to people immediately after they complete an SMS OTP authentication (relevant context) to capitalize on people’s focus on authentication and security.
- Educate people and raise awareness about passkeys as a new and more secure authentication method available to them.
Outcomes
- By increasing passkey adoption, this pattern:
- helps reduce SMS OTP operational costs by eliminating the need for SMS infrastructure and the associated costs, for example, SMS fees, maintenance, and support.
- helps enhance people’s experiences with passkeys’ seamless and convenient authentication experience, leading to higher user satisfaction and increased conversion rates.
- helps reduce security risks associated with common vulnerabilities associated with SMS OTP, such as SIM swap attacks and the interception of one-time codes.
- reduces user errors associated with entering incorrect verification codes, mistyping codes, or experiencing delays in receiving SMS codes.
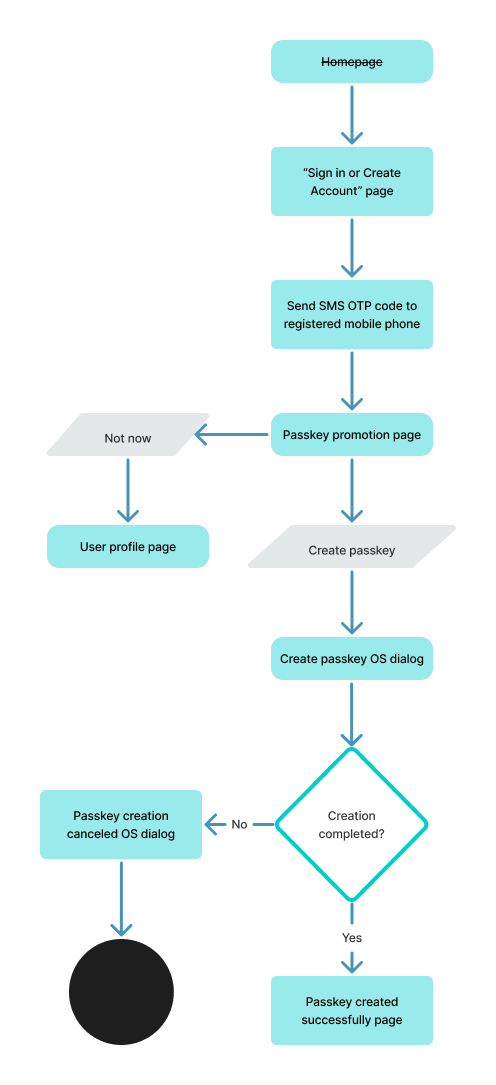
Flow: schematic
Flow steps
- The user initiates the Sign-in experience.
On the service provider’s homepage, the user initiates the sign-in experience using the discoverable call to action to Sign in or create an account. - The system displays the Sign in or create account page, and the user enters their username and password.
After the user selects the Sign in or create account button, the system displays a page with editable fields for the username and password and an action button to sign in. The user enters a valid username and password and selects Sign in to continue the sign-in process. - The user enters their username and password.
- The system triggers SMS OTP authentication, and the user verifies their identity.
The system recognizes the username and password and triggers SMS OTP authentication. DigitalFiles triggers SMS OTP when the user uses a new device to sign in after identity proofing; however, the service provider could have integrated SMS OTP in different scenarios, for example, periodic reauthentication or suspicious activity. A verification code is sent to the mobile phone number associated with the user’s account. The user retrieves the code from their messages and enters it into the designated fields on the authentication page. - Verification code is entered.
Upon submission, the system validates the code against the one generated and sent to the user. If the code matches and was entered within the designated time frame, the user is granted access to their account. If the code does not match (for example, code entered incorrectly), the user is prompted to re-enter the code or to request a new one. - The system introduces passkeys after SMS OTP verification.
Following SMS OTP verification, the system introduces passkeys as an alternative authentication method using the passkey hero prompt. The FIDO-recommended passkey hero includes specific symbols, headlines, messaging, and calls to action that were found via user research to be the most helpful information about passkeys after users have completed the SMS OTP authentication process. Use the passkey hero messaging, adding and codes to the end of the headline. - The user creates a passkey for the displayed email address using screen lock (OS dialogue).
The system triggers the passkey OS dialogues to allow users the choice to create or decline to create a passkey for the specified email. - Use your screen lock dialog.
If the user opts to create a passkey by selecting the Continue button on Android or the Confirm button on iOS, the mobile OS prompts the user to use their screen lock to authenticate. If the user opts to decline to create a passkey by selecting the Cancel button on Android or the X button in the upper right corner of the iOS dialogue, the mobile OS exits the creation process and removes the OS overlay. - Use your screen lock dialog, success.
If the passkey creation is successful, a passkey creation confirmation message from the OS is displayed and disappears automatically; no action is needed from the user. - The system confirms the successful creation of the passkey.
The system confirms the passkey’s successful creation with a success message. To acknowledge this, use the FIDO-recommended symbols, headlines, messaging, and actions. The primary purpose of the FIDO-recommended success message is two-fold: (1) provide users with a clear and positive confirmation that the passkey creation process has been completed successfully, and (2) reinforce user ownership, drive engagement, facilitate maintenance, and ultimately encourage the long-term adoption of passkeys as a secure and user-friendly authentication solution.
Flow: video
Flow: prototype
To view full screen, hover over the prototype, then select the expand icon.
Content
Copy and edit user-tested content examples to suit your needs.
With passkeys, you don’t need to remember complex passwords and codes.
What are passkeys?
Passkeys are encrypted digital keys you create using your fingerprint, face, or screen lock.
Where are passkeys saved?
Passkeys are saved in your credential manager, so you can sign in on other devices.
UX Research
Perception of passkeys as a replacement to SMS OTP (summary)
User experience research found that the FIDO-recommended images and messaging used to introduce passkeys after SMS OTP identity-proofing motivated participants to create a passkey. The findings combined with a 60% conversion rate (9/16 participants), suggest that the clear, concise messaging highlighting the convenience and security benefits of passkeys, effectively motivated participants to adopt passkeys to replace SMS OTP authentication.
“This [passkey hero] would motivate me to want to click ‘Create Passkey.’ Just the first explanation of getting rid of complex passwords and codes and just having something I recognize as quick and easy, like my fingerprint, face, or lock screen, and it’s stored in the same place as all the rest of my passwords.”
—Phase 2 -Participant 2 (age: 24), Android (Chrome)
Response to passkey introduction
Participants positively perceived the simplicity and convenience of passkeys, appreciating the idea of using biometrics instead of complex passwords and codes (why use a passkey?). Their comfort and trust in biometric authentication influenced their perception of passkeys as a secure and user-friendly alternative. In addition, participants recognized the encryption aspect of passkeys, which added to their perceived security advantages over SMS OTP authentication (what is a passkey?).
“So I see a passkey as more of a solution to all of that [managing passwords], where I can still keep the complexity but make it easier for myself.”
—Phase 3 -Participant 2 (age: 29), Android (Chrome)
User research found that participants had a positive view of integrating passkeys with existing password management tools and their use across different devices (where are passkeys saved?). This was due to participants’ familiarity with credential managers, which centralize credential management and provide a familiar interface. In addition, some participants voiced their interest in the cross-device functionality and raised questions about the compatibility and interoperability of passkeys across different devices and platforms.
“I just think that’s [passkey interoperability] very innovative if you sign in for a different device from your laptop. I think that could be an efficient way to sign in to the device.”
—Phase 3 -Participant 6 (age: 32), Android (Chrome)
Participants accurately inferred that passkeys offered a new sign-in option using their device’s authentication system, which was considered familiar and trusted. Therefore, based on their experience with biometric authentication, participants anticipated the creation and sign-in process to be fast, easy, and secure. While most participants opted to create a passkey (60% conversion rate), a few opted out, preferring the tangibility and familiarity of traditional passwords and codes.
Compared to SMS OTP authentication, user research suggests that participants’ positive experiences with biometric authentication played a key role in shaping their more favorable perceptions of the security and usability of passkeys. This familiarity helped overcome any initial uncertainty or unfamiliarity with the new passkey terminology and concept.
“The passkey was definitely simpler, and I didn’t have to go look at another account to sign in. I like that. Again, with the passkey, it was very easy to just import my username and password, and I didn’t have to navigate from the task at hand to go check my text messages or check my emails.”
—Phase 2 -Participant 7 (age: 38), iPhone (Safari)
Evaluating passkey performance (creation and sign-in)
Participants consistently described the process of creating a passkey as easy and straightforward, requiring minimal effort. In addition, participants found the tip on managing passkeys to be helpful, as it addressed their expectation of having control over their passkeys, including the ability to change, delete, and add biometric authentication methods, thereby reassuring them of their control over their online accounts.
“The first time it was fast, second time was even faster. Or I should say the first time was really fast and the second time was really, really fast because it took like almost no time.”
—Phase 3-Participant 8 (age: 23), iPhone (Safari)
“[Passkeys are more secure] Because it’s trying to verify that it’s me. I think 2FA is just verifying that it’s my device rather than verifying it’s me.”
—Phase 3-Participant 8 (age: 23), iPhone (Safari)
After experiencing the sign-in process with both authentication approaches (SMS OTP and passkeys), participants found passkeys to be notably easier and more efficient. However, it is important to note that some participants noticed that signing in with a passkey differs from the biometric sign-in experience support on their devices, with passkeys requiring an additional tap.
Roll-out strategy
To reduce costs to certain lines of business, some service providers choose to roll out this pattern first (along with Sign In with a Passkey).
Ecosystem
- Passkeys might require specific hardware or software support on user's devices. Ensure that users are aware of the compatibility requirements for using passkeys and provide guidance on compatible devices and browsers.
- In the native mobile app context, signing in with a passkey differs from the biometric sign-in experience that has existed for many years. Signing in with a passkey requires an additional tap.
Security
- Passkeys mitigate phishing and the risk of credential theft by eliminating the need for users to enter phishable passwords or phishable one-time codes.
- DigitalBiz gracefully falls back to an email OTP. The graceful fallback option you choose should match your unique security and business goals. Plan your UX in accordance with your unique security and business needs. The guidelines focus on UX concepts that are unique to FIDO with synced passkeys. You will see various forms of identity proofing and non-FIDO authentication examples throughout this work. The guidelines do not intend to prescribe security guidelines for identity proofing or other non-FIDO authentication mechanisms as they are unique to each relying party (RP) and based on their own unique business needs and security policy.





