Passkey Management UI: Best Practices for Combining All Passkey Types
Overview
Topics: consumer, multiple passkey types, passkey management interface
Customer journey: Awareness > Consideration > Enrollment > Management > Authentication
Created: 24 May 2024
Management of different passkey types that exist in the same user interface, under the heading Passkeys.
Add management of different passkey types
This page covers steps to add management of different passkey types that exist in the same user interface, under the heading Passkeys.
- Passkeys can live on devices or security keys.
- The APIs for the browser and operating system are the same for all passkey types.
- Most devices, such as phones and laptops, store passkeys that are synced to a credential manager. The technical term is synced passkeys. For all passkey types on devices, the term for the end users is passkeys on your devices.
- Most hardware security keys contain passkeys that are not synced to a cloud service or server. The technical term is device-bound passkeys. For all passkey types on security keys, the term for end users is passkeys on security keys.
- When creating interfaces for end users to manage passkeys, use passkeys on devices and passkeys on security keys not synced passkeys and device-bound passkeys as these are technical terms not meant for end users.
Outcomes
- Simplified end user interface for all passkey types.
- Alignment with the long-term direction of passkeys and APIs.
- Leverage the complete range of options that passkeys and the APIs offer.
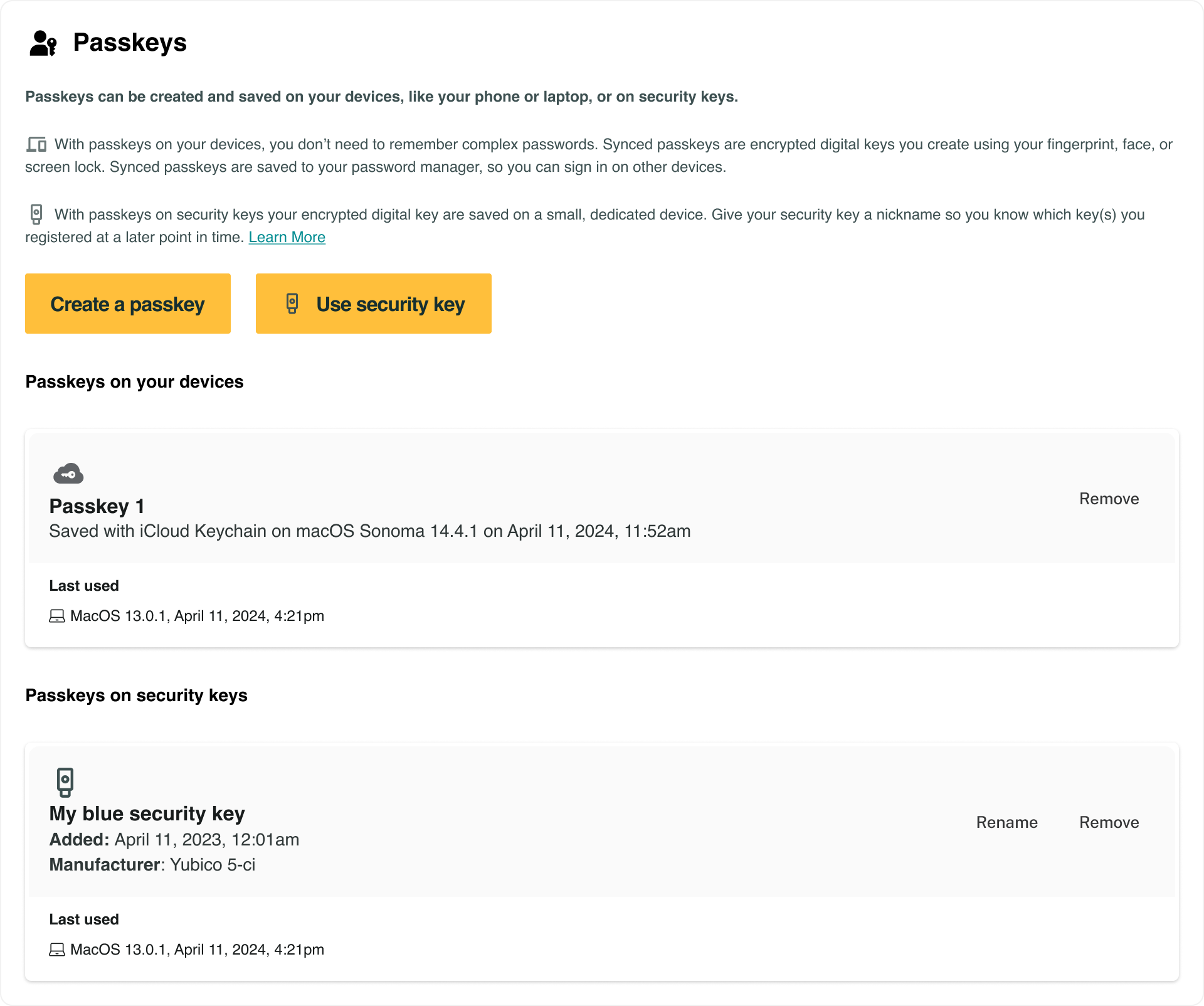
Flow: empty state
The management of different types of passkeys on user devices or security keys, exists in the same user interface under the heading Passkeys.
End users find the icons for devices (laptop and phone) and security keys (USB key) helpful and intuitive. Some users do not yet associate passkeys with hardware security keys. To make the enrollment of security keys more discoverable, include a separate call to action to Use a security key and include a USB security key icon in the call to action.
Flow: filled state
The end-user management of different passkey types on user devices or security keys, exists in the same user interface, under the heading Passkeys.
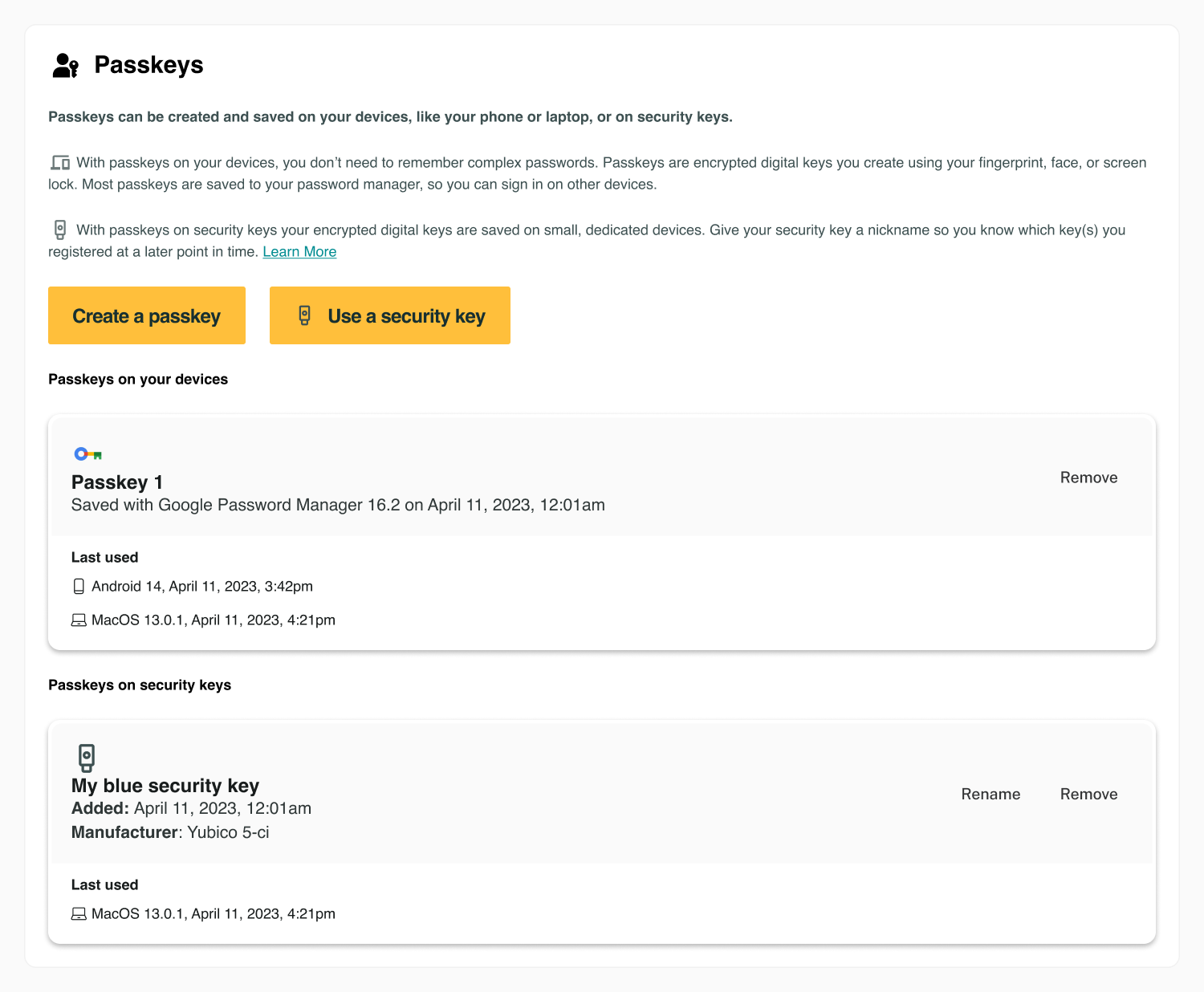
Passkeys on user devices, such as laptops or phones, are grouped under the heading Passkeys on your devices. Passkeys on hardware security keys are grouped under the heading Passkeys on security keys use the icon (logo) of the credential manager for passkeys on devices. Use the icon (logo) of a USB security key for a passkey on a security key.
Flow: future state
As passkeys become more familiar to people over time, and additional browser API controls are in place, use a single call to action to create all passkey types on devices or security keys.
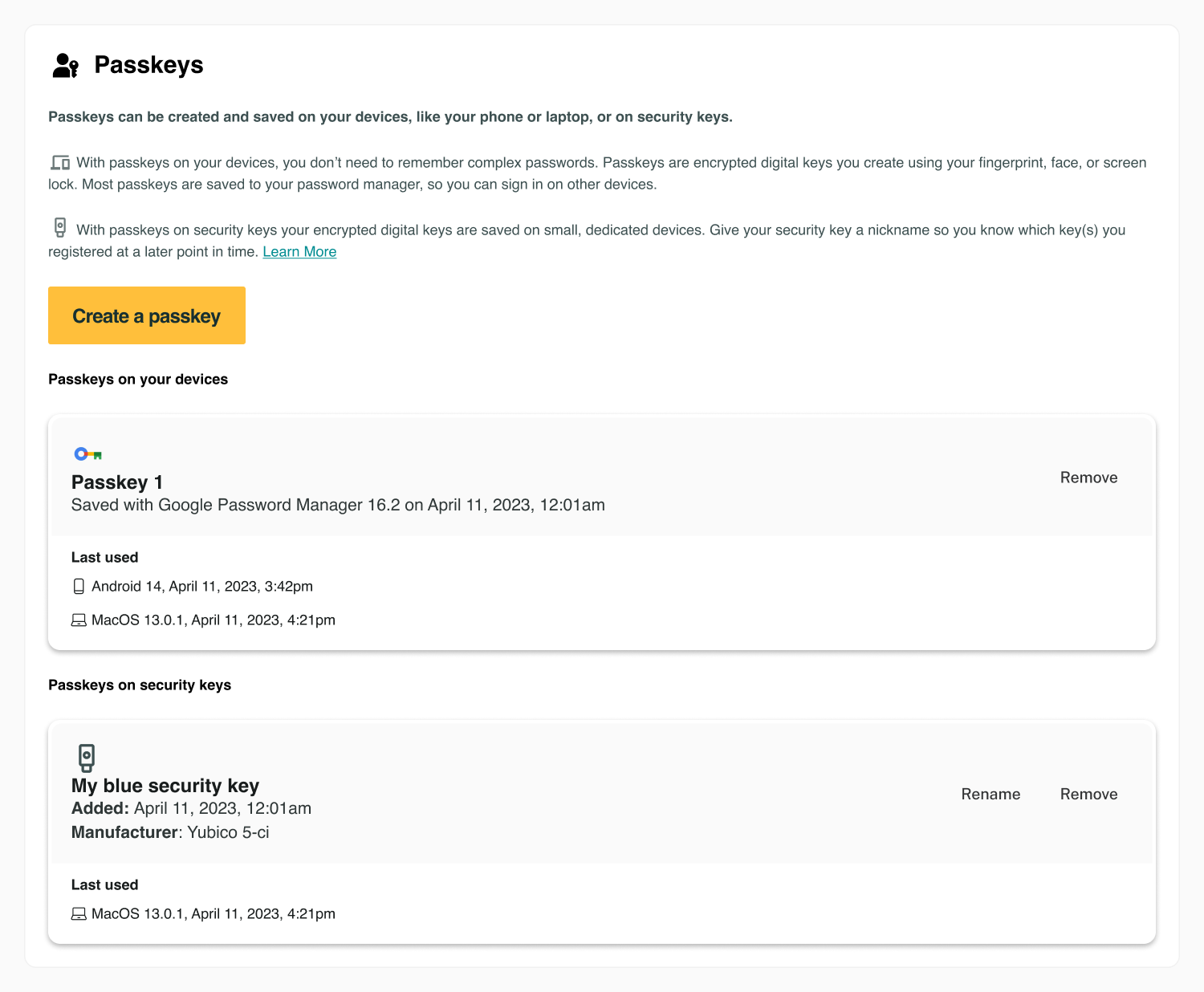
When using this approach, you will not be able to prompt to name the security key before enrolling it. Prompt to name the security key after enrollment.
Flow: video
Flow: prototype
To view full screen, hover over the prototype, then select the expand icon.
Content
Copy and edit user-tested content examples to suit your needs.
Passkeys
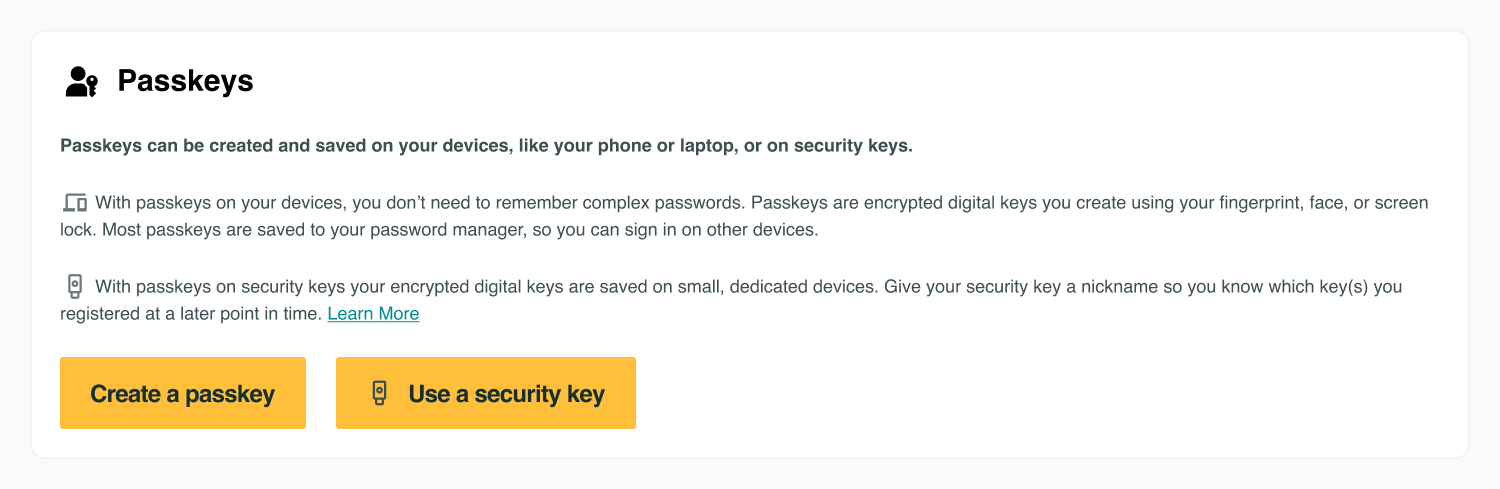
Passkeys can be created and saved on your devices, like your phone or laptop, or on security keys.
With passkeys on your devices, you don’t need to remember complex passwords. Passkeys are encrypted digital keys you create using your fingerprint, face, or screen lock. Most passkeys are saved to your credential manager, so you can sign in on other devices.
With security keys your encrypted digital key stays on a small, dedicated device. Give your security key a nickname so you know which keys you registered at a later point in time. Learn More
Create a passkey
Use a security key
UX Research
User experience research revealed that users had a perception of passkeys as technical elements that reside on phones, laptops, or USB keys (summary). User experience research also found that the clear, concise messaging describing the types of passkeys available effectively motivated participants to create and use a range of passkey types.
- Ensure that passkey options are prominently displayed within user account settings adjacent to other authentication modalities and consistently styled across platforms.
- Use commonly understood icons for passkeys on your devices (laptop and phone) and passkeys on security keys (USB key).
- Introduce passkey concepts gradually. Begin with basic benefits and usage instructions, followed by a Learn More link for those interested in deeper details. Refer to Awareness of Security Keys as an Authentication Option for detailed Learn more content.
Roll-out strategy
- Service providers who support passkeys on security keys should place the management interface under a heading called Passkeys even if they do not yet support passkeys on your devices.
- Service providers who support passkeys on devices and passkeys on security keys should allow people to manage them within the same user interface, under the heading Passkeys. The heading should include the passkey icon.
- As passkeys become more familiar to people over time, service providers can use a single call to action to create any type of passkey.
Ecosystem
Passkeys stored by Windows are device-bound and not synced across devices.
Security
- FIDO Alliance conducted adjacent research with findings that suggest use of passkeys on devices will lead to more use of passkeys on security keys.
- The FIDO Alliance acknowledges passkeys on security keys as the gold standard of authentication security.
- Passkeys on your devices can be Authentication Assurance Level 2 (AAL2).
- Passkeys on security keys can be Authentication Assurance Level 3 (AAL3).
- Federal Information Processing Standards (FIPS) categorize security into four levels, giving organizations the ability to choose passkeys that meet their specific security requirements.
- Use certified passkeys on security keys to maximize security. These passkeys vary in certification, with some meeting stringent FIPS standards, ensuring they meet precise security requirements and offer dependable protection.
- WebAuthn employs security flags to tailor authentication to specific scenarios, enhancing security for actions like User Presence (UP), User Verification (UV), and Backup Eligibility and Backup State.
Additional resources
- Authentication Assurance Level (AAL)
- Federal Information Processing Standards (FIPS)
- User Presence (UP), User Verification (UV), and Backup Eligibility and Backup State





