Troubleshoot Ecosystem Inconsistencies
This page offers troubleshooting tips for ecosystem inconsistencies related to implementation of support for passkeys.
Breaking changes in the ecosystem can block passkey use
For passkeys to function properly, all five of the following components need to work together. Breaking changes to any of these components might block passkey use.
- A relying party (typically a website)
- Operating systems
- Browsers
- Credential providers
- Hardware
Steps to reproduce
There are no known breaking changes.
Guidance
The FIDO-dev Group is a discussion list that supports the open internet community to better understand the technical specifications and collect feedback from real-world adoption experience. You can subscribe for free.
Related resources
- Technical discussion of changes to autofill behavior in iOS 17.4
- FIDO-dev Group
- FIDO-dev Group
Inconsistent experience across the ecosystem might create confusion
The passkey experience varies slightly for each operating system and credential manager.
Steps to reproduce
- Visit the Passkey operating system dialogs kit in FIDO's Figma UI Kits and view the passkey user interfaces to note the differences.
- Create passkeys on various operating system and credential managers and note of the differences.
- Sign in with passkeys on various operating systems and with various credential managers and note the differences.
Guidance
By examining various combinations of operating systems and credential managers, you can gain a sense of the differences in operating systems and credential managers with regards to implementation of support for passkeys. With this understanding, you can create messaging for your service that compliments messaging across operating systems and credential managers.
For example, the following messages are from various operating system dialog boxes.
- Android: "Use your screen lock" when signing in.
- Apple: "
{Browser}is trying to verify your identity on{rp id}. Touch ID or enter your password to allow this." - Windows: "Making sure it's you. Sign in to
{rp id}as{username}".
Your organization can use browser User-Agent (UA) information to ensure your messaging matches the operating system messaging. In practice however, this is not always necessary. The FIDO Alliance ran rigorous user testing to create of messages that your organization can use, that are designed to work in concert with operating systems dialog messages. You can view this messaging throughout the Design Guidelines.
One example is that Android and Apple allow pin, fingerprint, and face inputs for passkey. However, while Android allows use of a pattern Apple iOS does not.
To help you understand the differences in passkey-related dialogs with regards to operating systems, credential managers, and browsers, refer to the Passkey operating system dialogs kit. This resource helps you examine the differences between prominent operating systems, credential managers, and browsers.
Related resources
It is impractical or impossible to test all ecosystem combinations
For passkeys to function properly, all of the following components need to work together. Breaking changes to any of these components might block passkey use.
- Operating systems
- Browsers
- Credential providers
- Hardware
There are many possible combinations of these components. For example, if there are four options for each component, a total of 256 combinations exist (44 = 256). If there are five options for each component, there are 1,024 combinations (45 = 1,024).
There are many combinations you can test in order to ensure they all work well for your end users. However, testing the latest and most popular combinations will typically cover the majority of use cases.
Steps to reproduce
- Visit the Passkey operating system dialogs kit and view the passkey user interfaces to note the differences.
- Create passkeys on various operating systems and credential managers and note the differences.
- Sign in with passkeys on various operating systems and credential managers and note the differences.
Guidance
Review your end user access logs to discover which operating systems, browsers, and hardware people are using the most. Focus your testing efforts on the most common combinations.
Review the Device Support page on passkeys.dev to view an updated list of operating systems and browsers that support passkeys.
The FIDO-dev Group is a discussion list that supports the open internet community to better understand the technical specifications and collect feedback from real-world adoption experience. You can subscribe for free.
Related resources
- Passkeys.dev: Device Support
- FIDO-dev Group
It is impractical to show all ecosystem combinations in Help resources
The passkey experience is slightly different for each operating system, browser, and credential manager.
Steps to reproduce
- Visit the Passkey operating system dialogs kit and view the passkey user interfaces to note the differences.
- Create passkeys on various operating systems and credential managers and note the differences.
- Sign in with passkeys on various operating systems and with various credential managers and note the differences.
Guidance
The FIDO Alliance ran rigorous user testing to create of messages that your organization can use, that are designed to work in concert with operating systems dialog messages. You can view this messaging throughout the Design Guidelines.
Related resources
- FIDO Alliance: Design Guidelines
- Passkey operating system dialogs kit
Sign in terminology used for payment confirmation might create confusion
Some credential managers use the term sign in for all passkey use, even in use cases for secure payment confirmation. When a service provider uses a passkey to verify a payment, the OS dialog box still displays sign in. This can confuse relying parties as to what action they are taking. However, the WebAuthn API does not allow edits to the UX copy.
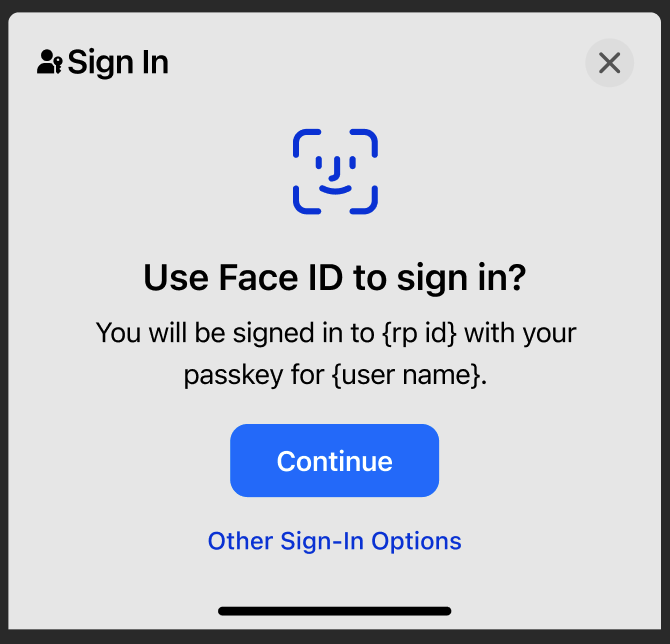
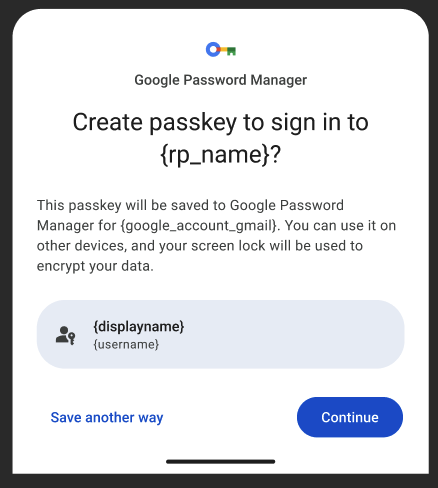
Steps to reproduce
- Imagine confirming an online credit card payment using passkeys.
- Notice that some credential managers use Sign in as the action in their user interfaces as opposed to Confirm payment.
Guidance
An API is now available to relying parties that allows them to change the action words a credential manager displays to users.
Related resources
Passkey sharing is only allowed by some credential managers
Some credential managers, such as Apple Passwords, allow passkeys to be AirDropped to Contacts.
Steps to reproduce
- Create a passkey on an Apple device.
- Share this passkey with a contact via AirDrop.
Notice that AirDrop requires the recipient to be a saved Contact and within physical proximity of the person sharing the passkey.
Guidance
The emphasis here is on your understanding of the ecosystem and end user education is not necessary.
Related resources
The following list of credential managers are FIDO Alliance members who offer the functionality to share passkeys.
- 1Password: How to share passkeys using 1Password
- Apple: Share passkeys and passwords securely with AirDrop on iPhone
- Keeper: Can passkeys be shared The following list of credential managers are FIDO Alliance members who offer the functionality to share passkeys.
Some people cannot use passkeys at work due to blocked access
It is common for large enterprises to issue and manage the devices people use for work. These managed devices can be phones, laptops, and other computing devices. Managed devices allow IT departments to limit, monitor, or control the functionality of the device. In some cases these controls can limit or block the use of passkeys.
Steps to reproduce
- Attempt to use passkeys on a device managed by your work.
- Notice if passkeys are allowed.
Guidance
The emphasis here is on your understanding of the ecosystem and end user education is not necessary.
Related resources
- Apple:
- The Using Passwords and Passkeys on Managed devices section of the Managing Passkeys article.
- Deploy passkeys at work video.
- Microsoft: Why doesn't my Windows device have some of the passkey's options described in the article? FAQ.
Using multiple credential providers might create confusion
End users can choose to use more than one credential manager. Although not common, end users can be confused by having more than one credential manager where their passkeys are stored.
Steps to reproduce
- Install more than one credential manager. For example, if you use Apple Passwords, install 1Password or Dashlane on macOS and use both.
- Ensure that both credential managers are available to use in the browser you choose, such as Safari or Chrome.
- Use a passkey.
- Notice that it can be confusing to determine which credential manager stores your passkey(s) and which is used to sign in.
- Notice that if
autofillis enabled on the service you are signing in to, the autofill options from one credential manager might position itself on top of another credential manager's input. Notice that this can make it difficult to explicitly use one and not the other. Notice that it can be difficult to see the usernames for each passkey in theautofillinterface because one credential manager might be blocking the other.
Guidance
The emphasis here is on your understanding of the ecosystem and end user education is not necessary. However, it can be helpful to inform your customer support team about this scenario so they can help troubleshoot issues with your end users.





